Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
You can’t assign more than one password policy In Windows 2003 which is applied at ___domain label but in Windows 2008 (All Versions) you can assign more than one password policy. Which is called “Fine-Grained Password Policy” in ADDS.
Make a note : You can’t apply the Fine-Grained Password Policy on OU label, only you can assign that with “user” and “Global Security group”.
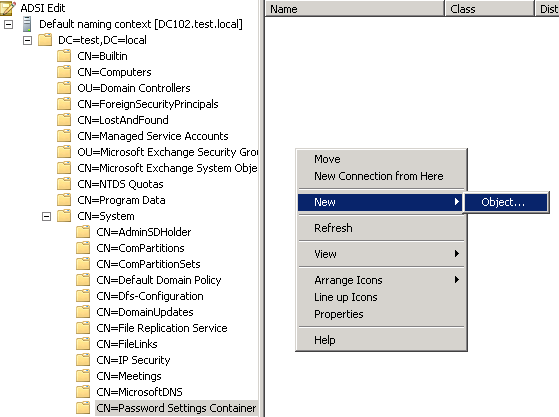
You can create the Fine-Grained Password Policy with ADSIEDIT.MSC.
One sample settings of a FGPP
Expanding base 'CN=biztest,CN=Password Settings Container,CN=System,DC=gs,DC=com'...
Getting 1 entries:
Dn: CN=biztest,CN=Password Settings Container,CN=System,DC=gs,DC=com
cn: biztest;
distinguishedName: CN=biztest,CN=Password Settings Container,CN=System,DC=gs,DC=com;
dSCorePropagationData: 0x0 = ( );
instanceType: 0x4 = ( WRITE );
msDS-LockoutDuration: 0:00:30:00;
msDS-LockoutObservationWindow: 0:00:30:00;
msDS-LockoutThreshold: 10;
msDS-MaximumPasswordAge: 14:00:00:00;
msDS-MinimumPasswordAge: 1:00:00:00;
msDS-MinimumPasswordLength: 12;
msDS-PasswordComplexityEnabled: TRUE;
msDS-PasswordHistoryLength: 14;
msDS-PasswordReversibleEncryptionEnabled: FALSE;
msDS-PasswordSettingsPrecedence: 1;
msDS-PSOAppliesTo: CN=nor,CN=Users,DC=gs,DC=com;
name: biztest;
objectCategory: CN=ms-DS-Password-Settings,CN=Schema,CN=Configuration,DC=gs,DC=com;
objectClass (2): top; msDS-PasswordSettings;
objectGUID: a542fe42-f9d8-44a2-9f2b-905a3dc83f48;
uSNChanged: 32931;
uSNCreated: 32927;
whenChanged: 12/7/2012 6:35:56 PM India Standard Time;
whenCreated: 12/7/2012 6:30:30 PM India Standard Time;
How to Manage Active Directory Password Policies in Windows Server 2008/R2
http://redmondmag.com/Articles/2011/08/01/Managing-Active-Directory-Password-Policies.aspx?Page=1
Find the below link for creating a Fine-Grained Password Policy
http://blog.thesysadmins.co.uk/active-directory-fine-grained-passwords-with-adsi-edit.html
http://showmehowtodoit.com/2012/step-by-step-fine-grained-password-policy-in-windows-2008/
Apply PSOs to Users and Global Security Groups
http://technet.microsoft.com/en-us/library/cc731589(WS.10).aspx
For more details, see the below links.
http://technet.microsoft.com/en-us/library/cc770394(WS.10).aspx
You can find the PSO setting with the dsquery command
C:\>dsquery * "CN=FirstFGPP,CN=Password Settings Container,CN=System,DC=contoso,DC=com" -scope base -attr *
**
We can test if the policy has been applied, run the below command
**
C:\>dsget user <user DN> -effectivepso