Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
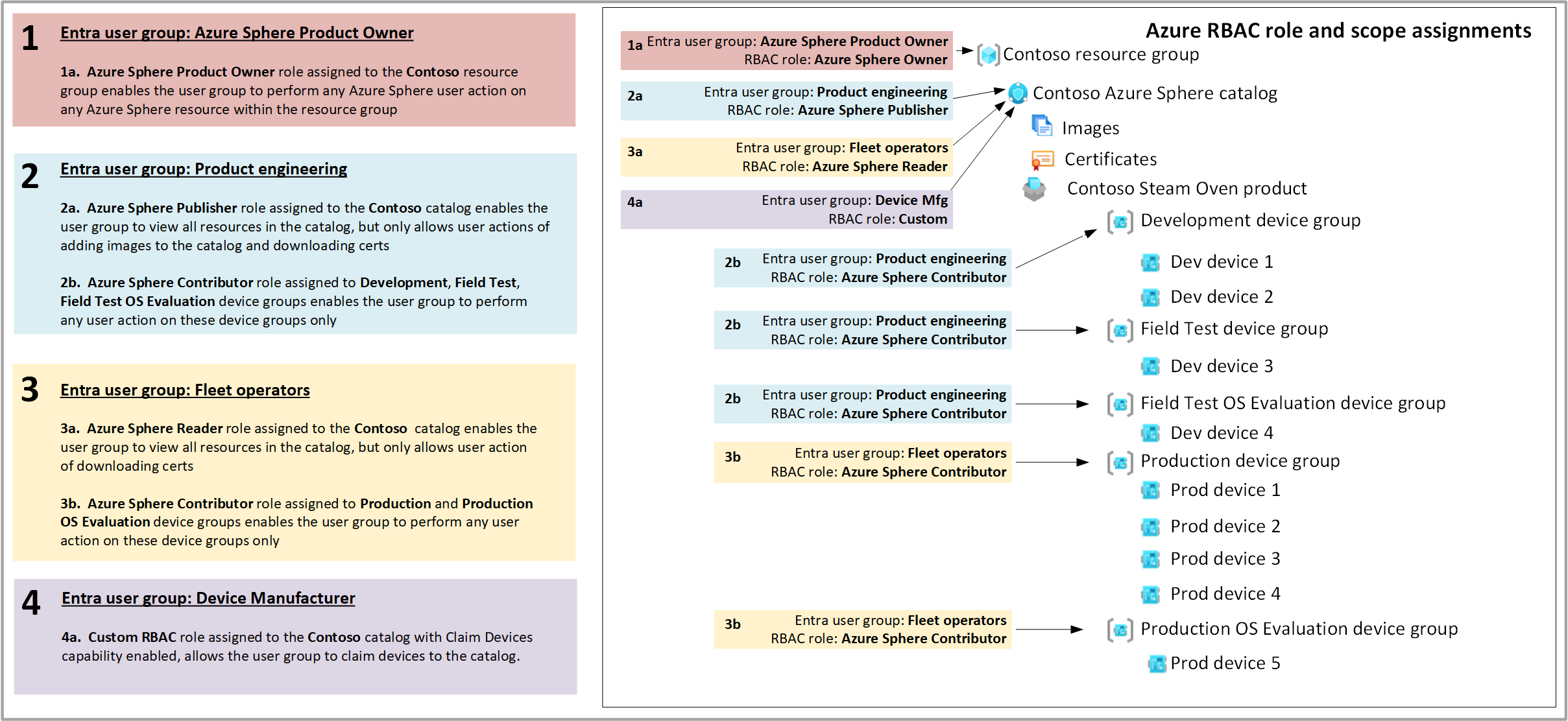
Many Azure Sphere customers want to configure RBAC access to enable engineering teams to perform development related functions on engineering owned devices and device groups, but prevent engineering teams from directly accessing production device groups typically managed by an operations team. The following scenario details how to configure a set of RBAC user groups and permissions to give both the engineering team and the operations team access only to the features and resources they need. Many Azure Sphere customers design their own Azure Sphere devices and manage them in the field, but will often partner with a contract manufacturer to build them. This business model often results in four distinct Azure Sphere user profiles:
- Azure Sphere Product Owner users – the highest privilege Azure Sphere user group for users who need to create, configure, and manage new Azure Sphere catalogs and their child resources, including claiming devices to catalogs (permanently associating the claimed devices with only that catalog), and integrating existing Azure Sphere (Legacy) tenants to Azure Sphere (Integrated) catalogs.
- Product Engineer users – for users who need privileges for items belonging to the catalog resource itself, such as images and certificates, but who should not have privileges for all device groups belonging to the catalog, such as the potentially sensitive Production device group. This user group is especially appropriate for product development users who download device capability files, move devices between the Development, Field Test, and Field Test OS Evaluation devices groups, and who deploy new software and potentially collect crash dump files in the Field Test and Field Test OS Evaluation device groups, but who are not authorized to manage production devices in the Production and Production OS Evaluation device groups.
- Fleet operator users – for users who manage the production device fleet, needing permissions to the Production device group where they will deploy new software and firmware images, potentially enable crash dump file collection, and to validate that OS retail eval releases work as expected in the Production OS Evaluation device group.
-
- Device manufacturer users – intended for a typical automated manufacturing process that claims newly manufactured devices to the device owner’s Azure Sphere catalog. The device manufacturer does not need to browse the catalog or perform any Azure Sphere user action other than the claim and bulk claim functions.
In keeping with Azure RBAC best practices, each user group has only those permissions that their business function requires. For example, the product engineering group can view all devices in the catalog, but can only take action on the devices in the engineering oriented device groups (Development, Field Test, and Field Test OS). The device manufacturer user can claim devices to the catalog, but cannot browse the catalog resources or take any further action on the claimed devices.
| User group | Azure RBAC role | Resource scope | Privileges enabled |
|---|---|---|---|
| Azure Sphere product owner | (1a) Azure Sphere Product Owner | Resource group | • Create, integrate, delete Azure Sphere catalogs within the resource group • Assign RBAC roles to Azure Sphere resources within the resource group • Perform any Azure Sphere user action • Configure and view Azure Monitor data for Azure Sphere device resources within the resource group |
| Product engineering | (2a) Azure Sphere Publisher | Azure Sphere catalog | • Read only access for all catalog resources • Add images to the catalog • Download device capabilities to enable device development • Download catalog certificate information |
| Product engineering | (2b) Azure Sphere Contributor | Development, Field Test, and Field Test OS Evaluation device groups | • Set device group properties for OS feed, 3rd party app deployment, and crash dump settings |
| • Deploy new images to devices in these groups • Assign and unassign devices to and from only these three groups • Configure and view Azure Monitor data for Azure Sphere device resources within the resource group |
|||
| Fleet operations | (3a) Azure Sphere Reader | Azure Sphere catalog | • Read only access for all catalog resources • Download catalog certificate information |
| Fleet operations | (3b) Azure Sphere Contributor | Production and Production OS Evaluation device groups | • Set device group properties for OS feed, 3rd party app deployment, and crash dump settings • Deploy new images to devices in these groups • Assign and unassign devices to and from only these two groups |
| Device Manufacturer | (4a) Azure RBAC Custom role (see additional details below) | Azure Sphere catalog | • Claim and bulk claim devices only |
Configuring an Azure RBAC custom role for the Device Manufacturer user While the Azure Sphere built-in RBAC roles provide for many of the common use cases, there are cases where Azure RBAC custom roles may be needed. Custom roles allow you to enable specific individual permitted actions for a user. For this sample scenario, we need to configure a custom RBAC role that allows the Device Manufacturer to claim devices to the catalog, but does not allow the Device Manufacturer to perform any other user actions or to browse the other resources in the catalog, such as images, products, or device groups.
To enable the device manufacturing user to claim devices, you would create a custom role that enables both the claim and bulk claim functions for the catalog.
| User action | Permission | Description |
|---|---|---|
| Claim | Write: Devices_CreateOrUpdate | Claim up to 5 devices at a time |
| Bulk Claim | Write: DeviceGroups_ClaimDevices | Claim more than 5 devices at a time |
Warning
Users who need to integrate Azure Sphere (Legacy) tenants to Azure Sphere (Integrated) catalogs must have either the Azure Sphere Contributor or the Azure Sphere Contributor role applied to the resource group that owns the subscription to which the tenant belongs.
While it is possible to assign a user an RBAC role only on a product or device group but not its parent catalog, the user will not be able to search for the product or device group, or its parent catalog, from their Azure home screen. They can only access the product or device group via a URL that points directly to it. For the sake of user convenience, we recommend that all users have at least Azure Sphere Reader access to the catalog.