Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In addition to native Active Directory support, Azure NetApp Files supports native integration with directory services including FreeIPA, OpenLDAP, and Red Hat Directory Server for lightweight directory access protocol (LDAP) directory servers. With native LDAP directory server support, you can achieve secure and scalable identity-based access control for NFS volumes in Linux environments.
Azure NetApp Files' LDAP integration simplifies file share access management by leveraging trusted directory services. It supports NFSv3 and NFSv4.1 protocols and uses DNS SRV record-based discovery for high availability and load balancing across LDAP servers. From a business perspective, this feature enhances:
- Compliance: Centralized identity management supports auditability and policy enforcement
- Efficiency: Reduces administrative overhead by unifying identity controls across Linux and NTFS systems
- Security: Supports LDAP over TLS, symmetric/asymmetric name mapping, and extended group memberships
- Seamless integration: Works with existing LDAP infrastructure
- Scalability: Supports large user and group directories
- Flexibility: Compatible with multiple LDAP implementations
Supported directory services
- FreeIPA: Ideal for secure, centralized identity management in Linux environments
- OpenLDAP: Lightweight and flexible directory service for custom deployments
- Red Hat Directory Server: Enterprise-grade LDAP service with advanced scalability and security features
Important
To configure LDAP with Active Directory, see Configure AD DS LDAP with extended groups for NFS volume access.
Architecture
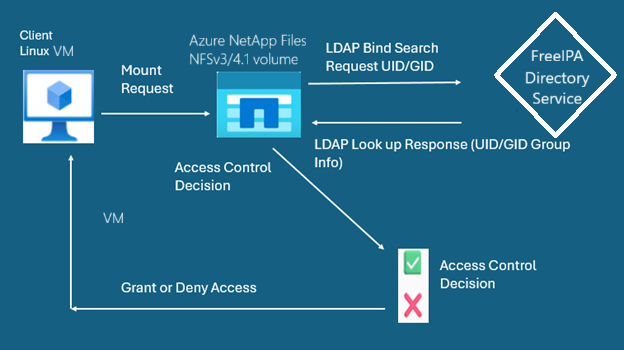
The following diagram outlines how Azure NetApp Files uses LDAP bind/search operations to authenticate users and enforce access control based on directory information.
The architecture involves the following components:
- Linux VM client: initiates an NFS mount request to Azure NetApp Files
- Azure NetApp Files volume: receives the mount request and performs LDAP queries
- LDAP directory server: responds to bind/search requests with user and group information
- Access control logic: enforces access decisions based on LDAP responses
Data flow
- Mount Request: The Linux VM sends an NFSv3 or NFSv4.1 mount request to Azure NetApp Files.
- LDAP Bind/Search: Azure NetApp Files sends a bind/search request to the LDAP server (FreeIPA, OpenLDAP, or RHDS) using the UID/GID.
- LDAP Response: The directory server returns user and group attributes.
- Access Control Decision: Azure NetApp Files evaluates the response and grants or denies access.
- Client Access: The decision is communicated back to the client.
Use cases
Each directory service appeals to different use cases in Azure NetApp Files.
FreeIPA
- Hybrid Linux environments: Ideal for enterprises using FreeIPA for centralized identity management across Linux systems in hybrid cloud deployments.
- HPC and analytics workloads: Supports secure authentication for high-performance computing clusters and analytics platforms that rely on FreeIPA.
- Kerberos integration: Enables environments that require Kerberos-based authentication for NFS workloads without Active Directory.
OpenLDAP
- Legacy application support: Perfect for organizations running legacy or custom applications that depend on OpenLDAP for identity services.
- Multi-platform identity management: Provides a lightweight, standards-based solution for managing access across Linux, UNIX, and containerized workloads.
- Cost-optimized deployments: Suitable for businesses seeking an open-source, flexible directory solution without the overhead of Active Directory.
Red Hat Directory Server
- Enterprise-grade security and compliance: Designed for organizations that require hardened, enterprise-supported LDAP services with strong security controls.
- Regulated industries: Ideal for financial, healthcare, and government sectors where compliance and vendor support are critical.
- Integration with Red Hat Ecosystem: Seamlessly fits into environments leveraging Red Hat Enterprise Linux and related solutions.
Considerations
- FreeIPA, OpenLDAP, and Red Hat Directory Server are supported with NFSv3 and NFSv4.1 volumes; they aren't currently supported with dual-protocol volumes.
- These directory services aren't currently supported with large volumes.
- You must configure the LDAP server before creating the volume.
- You can only configure FreeIPA, OpenLDAP, or Red Hat Directory Server on new NFS volumes. You can't convert existing volumes to use these directory services.
- Kerberos isn't currently supported with FreeIPA, OpenLDAP, or Red Hat Directory Server.
Register the feature
Support for FreeIPA, OpenLDAP, and Red Hat Directory Server is currently in preview. Before connecting your NFS volumes to one of these directory servers, you must register the feature:
Register the feature:
Register-AzProviderFeature -ProviderNamespace Microsoft.NetApp -FeatureName ANFOpenLDAPCheck the status of the feature registration:
Note
The RegistrationState can remain in the
Registeringstate for up to 60 minutes before changing toRegistered. Wait until the status isRegisteredbefore continuing.Get-AzProviderFeature -ProviderNamespace Microsoft.NetApp -FeatureName ANFOpenLDAP
You can also use Azure CLI commands az feature register and az feature show to register the feature and display the registration status.
Create the LDAP server
You must first create the LDAP server before you can connect it to Azure NetApp Files. Follow the instructions for the relevant server:
- To configure FreeIPA, see the FreeIPA QuickStart Guide then follow Red Hat's guidance.
- For OpenLDAP, see OpenLDAP documentation.
- For Red Hat Directory Server, follow the Red Hat documentation. For more information, see the install guide for 389 Directory Server.
Configure the LDAP connection in Azure NetApp Files
In the Azure portal, navigate to LDAP connections under Azure NetApp Files.
Create the new LDAP connection.
In the new menu, provide:
- Domain: The ___domain name serves as the base DN.
- LDAP servers: The IP address of the LDAP server.
- LDAP over TLS: Optionally, check the box to enable LDAP over TLS for secure communication. For more information, see Configure LDAP over TLS.
- Server CA certificate: The certification authority certificate. This option is required if you use LDAP over TLS.
- Certificate CN Host: The common name server of the host, for example contoso.server.com.
Select Save.
Once you configure the LDAP connection, you can create an NFS volume.
Validate the LDAP connection
- To validate the connection, navigate to the volume overview for the volume using the LDAP connection.
- Select LDAP connection then LDAP Group ID List.
- In the Username field, enter the username provided when you configured the LDAP server. Select Get Group IDs. Ensure the group IDs match the client and server.