Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure DevOps Services
Azure DevOps provides group-based access levels for Microsoft Entra groups and Azure DevOps groups, allowing you to manage permissions efficiently by assigning access levels to entire groups of users. This article explains how to add a group rule to assign an access level to a group of users.
Assign a group rule to manage both access levels and project memberships. When a user belongs to multiple rules or Microsoft Entra groups with different access levels, they receive the highest level.
Example: If a user belongs to two Microsoft Entra groups—one assigning Stakeholder and the other Basic—the user receives Basic access.
When a user leaves a Microsoft Entra group, Azure DevOps adjusts their access level according to the group's defined rules. If the group was the user's sole source of access, Azure DevOps automatically removes them from the organization. If the user belongs to other groups, their access level and permissions are reevaluated.
Note
- Azure DevOps applies resources granted by group rules to all members of the configured group. However, access and permissions take effect only after the user signs in to the organization for the first time.
- Changes made to project readers through group rules don't persist. To adjust project readers, consider alternative methods such as direct assignment or custom security groups.
- Regularly review the rules listed on the Group rules tab of the Users page. Changes to Microsoft Entra ID group membership appear during the next group rule re-evaluation, which occurs:
- On-demand when you trigger it manually
- Automatically when you modify a group rule
- Automatically every 24 hours. Azure DevOps updates Microsoft Entra group membership every hour, but Microsoft Entra ID might take up to 24 hours to update dynamic group membership.
- Group rules for licensing currently don't apply to service principals and managed identities. To assign an access level to a service principal or managed identity, assign it directly rather than through group membership. For more information, see Use service principals & managed identities in Azure DevOps.
Prerequisites
| Category | Requirements |
|---|---|
| Permissions | Member of the Project Collection Administrators group. Organization owners are automatically members of this group. |
| Microsoft Entra | Member of the Microsoft Entra ID that backs your organization. For more information, see Access via Microsoft Entra FAQs. Microsoft Entra guests can't search the Microsoft Entra ID in the manner required by Azure DevOps |
Add a group rule
Sign in to your organization (
https://dev.azure.com/{Your_Organization}).Select
 Organization settings.
Organization settings.Select Users > Group rules > Add a group rule. This view shows you all of your created group rules.
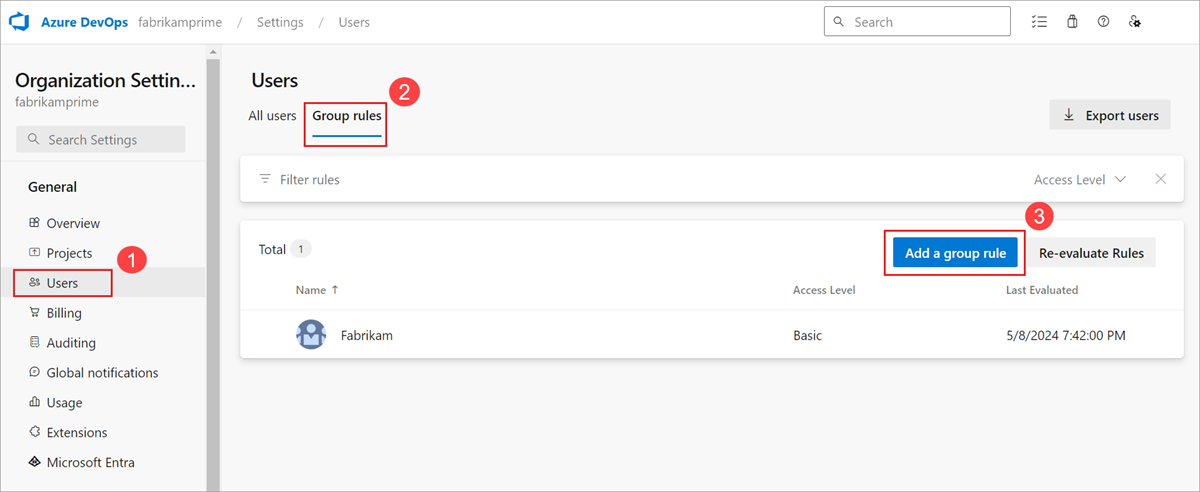
Group rules appear only if you're a member of the Project Collection Administrators group.
Complete the dialog box for the group for which you want to create a rule. Include an access level for the group and any optional project access for the group. Select Add.

A notification displays, showing the rule's status and outcome. If the assignment fails, select View status to see the details.
Important
- Users don't appear in All users until they attempt to sign in for the first time.
Access level changes
- When a user signs in, group rules automatically adjust their access level if the rule assigns a higher level than their current one. For example: A user with Stakeholder access upgrades to Basic if a group rule assigns Basic.
- If a user already has a higher access level than what the group rule provides, their access stays the same. For example: A user manually assigned Basic access doesn't downgrade when a group rule assigns Stakeholder.
Manage group members
Group rules for Microsoft Entra ID groups manage membership in the Azure portal. Group rules for Azure DevOps groups manage membership on the Group rules screen.
Select Group rules >
 > Manage members.
> Manage members.
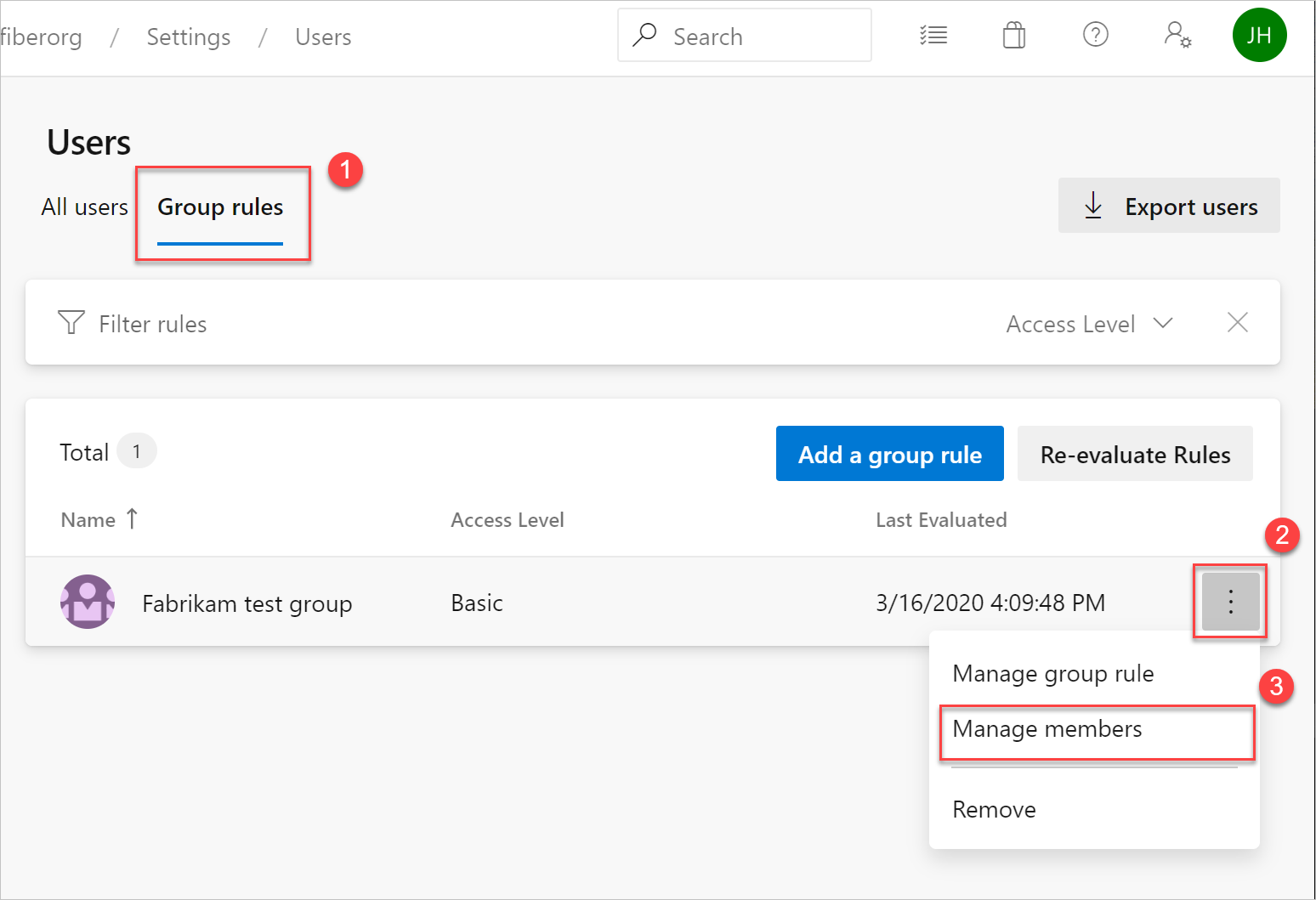
Add members, and then select Add.

Verify group rule
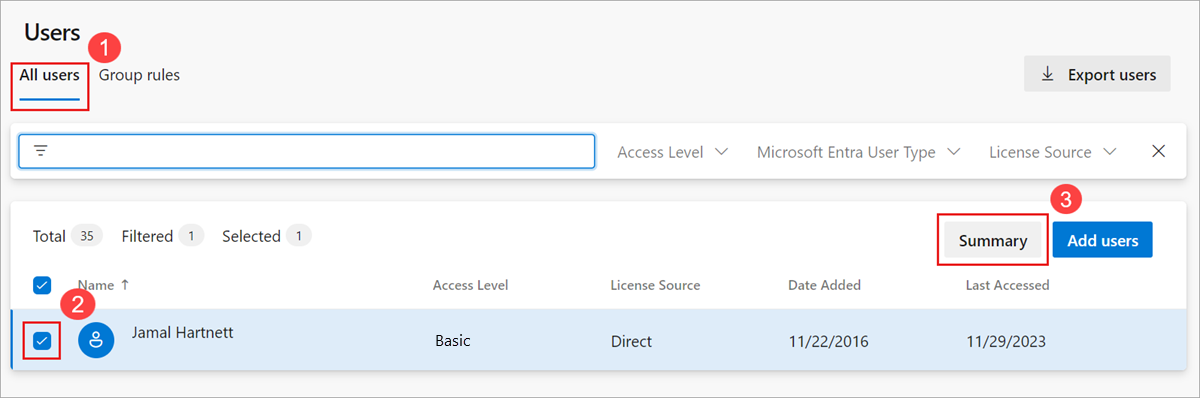
Verify that the resources apply to each group and individual user:
Select All users.
Highlight a user.
Select Summary.
Remove direct assignments
When a user has a direct assignment and a group rule grants a higher access level, Azure DevOps automatically upgrades the user to the higher level. To manage access levels exclusively through group rules, remove all direct assignments.
Sign in to your organization (
https://dev.azure.com/{Your_Organization}).Select
 Organization settings.
Organization settings.
Select Users.

Select all users with resources for management only by groups.
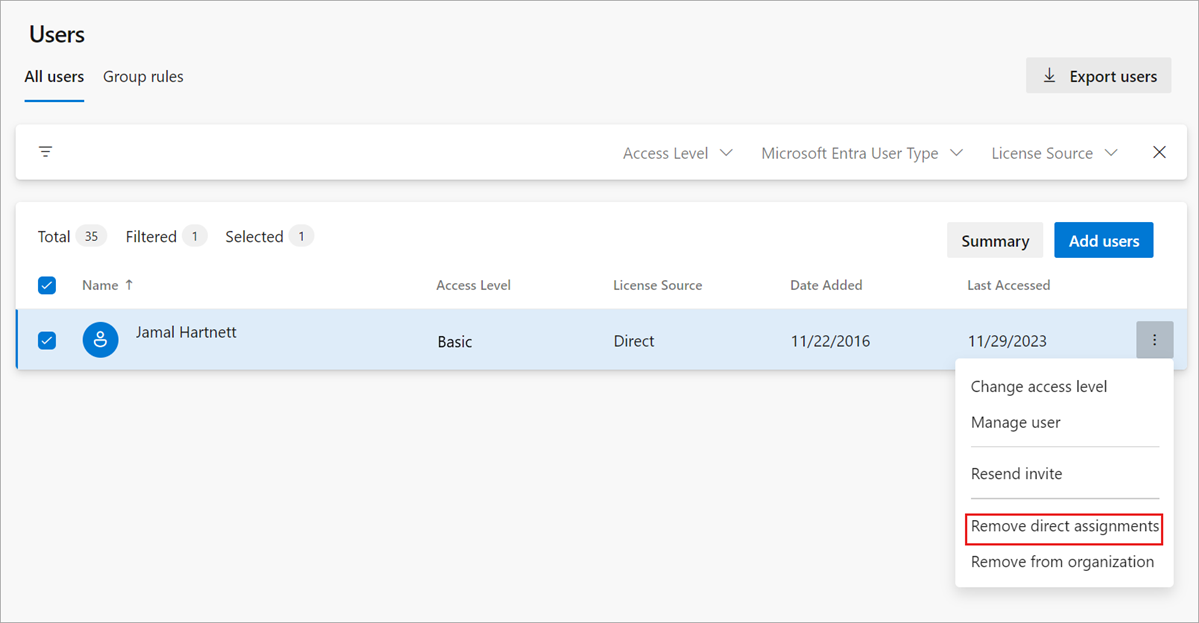
To confirm that you want to remove the direct assignments, select Remove.

If a user isn't a member of any groups, then the user isn't affected.
FAQs
Q: How do Visual Studio Subscriptions work with group rules?
A: Visual Studio Subscribers are always directly assigned via the Visual Studio Admin Portal and take precedence in Azure DevOps over access levels assigned directly or via group rules. When you view these users from the Users Hub, the License Source always shows as Direct. The only exception is Visual Studio Professional subscribers who are assigned Basic + Test Plans. Since Basic + Test Plans provides more access in Azure DevOps, it takes precedence over a Visual Studio Professional subscription. You can't configure a group rule to assign GitHub Enterprise access because GitHub assigns that license directly through its portal.
Q: How do GitHub Enterprise licenses work with group rules?
A:
- Azure DevOps checks whether a user has a GitHub Enterprise license when they sign in. It might take up to 24 hours for their access level to update to GitHub Enterprise. Users with GitHub Enterprise automatically receive the GitHub Enterprise access level, which equals Basic access.
- If a GitHub Enterprise user needs access to Test Plans, assign the Basic + Test Plans license directly or through a group rule.
- You can't configure a group rule to assign GitHub Enterprise access because GitHub assigns that license directly through its portal.
- When a user no longer has a valid GitHub Enterprise license:
- If your organization configures group rules: The user receives the access specified by their group membership.
- If your organization doesn't configure group rules: The user receives the organization’s default access level.