Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Important
Some information in this article relates to a prereleased product which might be substantially modified before it's commercially released. Microsoft makes no warranties, express or implied, with respect to the information provided here.
Threat intelligence analysts face several challenges in delivering insightful, actionable, contextualized intelligence. The task of developing threat intelligence briefings involves collecting information from various threat feeds, tools, and portals; filtering and correlating this information; and analyzing and mapping organizational risks. These activities happen before analysts can even start developing the report itself and generating insights for when they deliver the briefing. By then, as these processes can take anywhere from hours to days, the threats facing the organization have already evolved, which can render the briefing obsolete.
This preview version of the Threat Intelligence Briefing Agent was developed in response to these pain points. The Threat Intelligence Briefing Agent in the Microsoft Security Copilot standalone portal generates threat intelligence briefings based on the latest threat actor activity and both internal and external vulnerability information—in a matter of minutes. The agent can help security teams save time by creating a customized, relevant report that provides key situational awareness for CISOs and managers, and a solid starting point for threat intelligence analysts for their threat defense work.
The agent leverages dynamic automation and deep generative AI along with its wealth of threat intelligence knowledge and signals. When building the briefing, the agent dynamically chooses the next step based on the outcome of the previous step, allowing it to decide in real-time what threat intelligence to include and prioritize. The agent then translates this technical information into a digestible report that can be consumed by various audiences.
The Threat Intelligence Briefing Agent is best suited for customers who have turned on Microsoft Defender External Attack Surface and Microsoft Defender for Endpoint, as the agent relies on signals and insights from these first-party integrations to deliver accurate and context-rich reports.
Prerequisites
Permissions
This agent can read data from Defender External Attack Surface Management and Defender Vulnerability Management.
Identity
This agent requires connection to an existing user account.
Products
Microsoft Security Copilot is needed to run this agent.
Plugins
The following plugin is needed to run this agent:
- Microsoft Threat Intelligence
The following plugin is optional to run this agent, but can add more context to the output:
- Microsoft Defender External Attack Surface Management
Role-based access
Owner and contributors can see the report generated by the Threat Intelligence Briefing Agent within the Microsoft Security Copilot agent library page.
Trigger
This agent runs at the set time interval when turned on, or manually when you want to run it.
Set up the agent
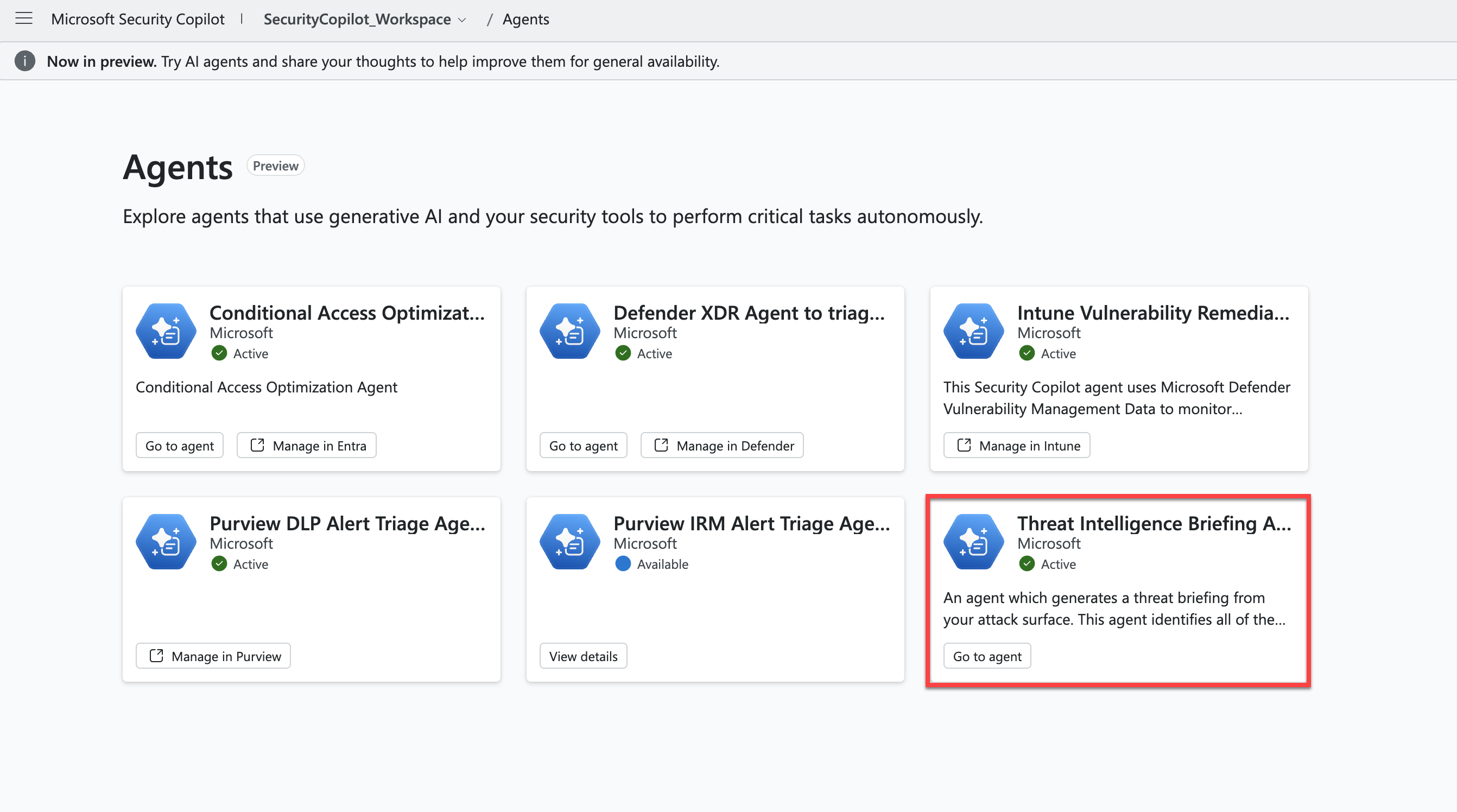
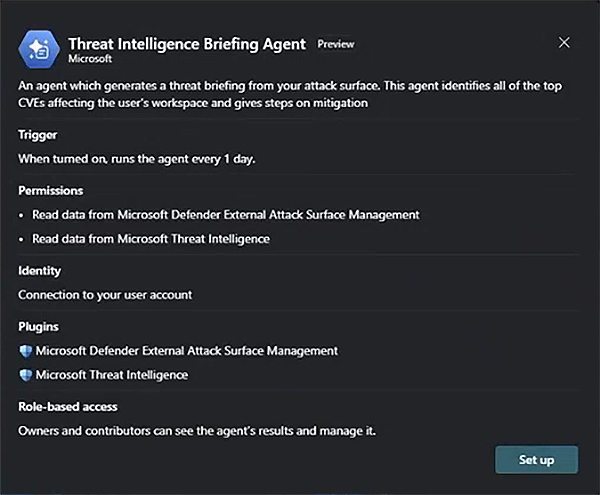
To run the Threat Intelligence Briefing Agent, first go the Agents page in the Microsoft Security Copilot standalone portal. Select View details under the Threat Intelligence Briefing Agent.
Connect a user account to the agent by selecting Next to open a new window where you can select the user account. After this, wait for the agent to finish setting up.
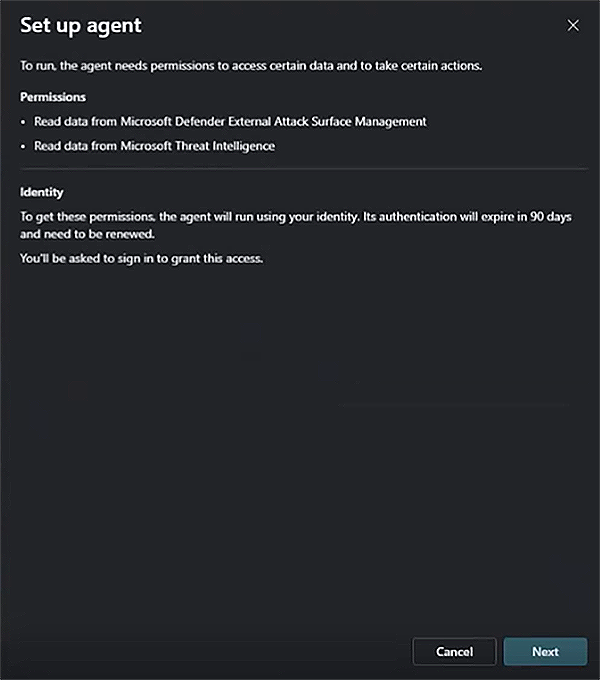
Specify the parameters to customize the output, then select Finish. You can edit these parameters later by selecting the three dots in the upper right section of the agent overview page.
- Insights to research – the number of vulnerabilities the agent researches for active threats
- Look back days – how far back the agent researches threats against your vulnerabilities
- Email – email address of user or distribution group that the briefing is sent to
- Region – scope of geographical area the agent checks for threats
- Industry – sector or industry that the agent checks for threats
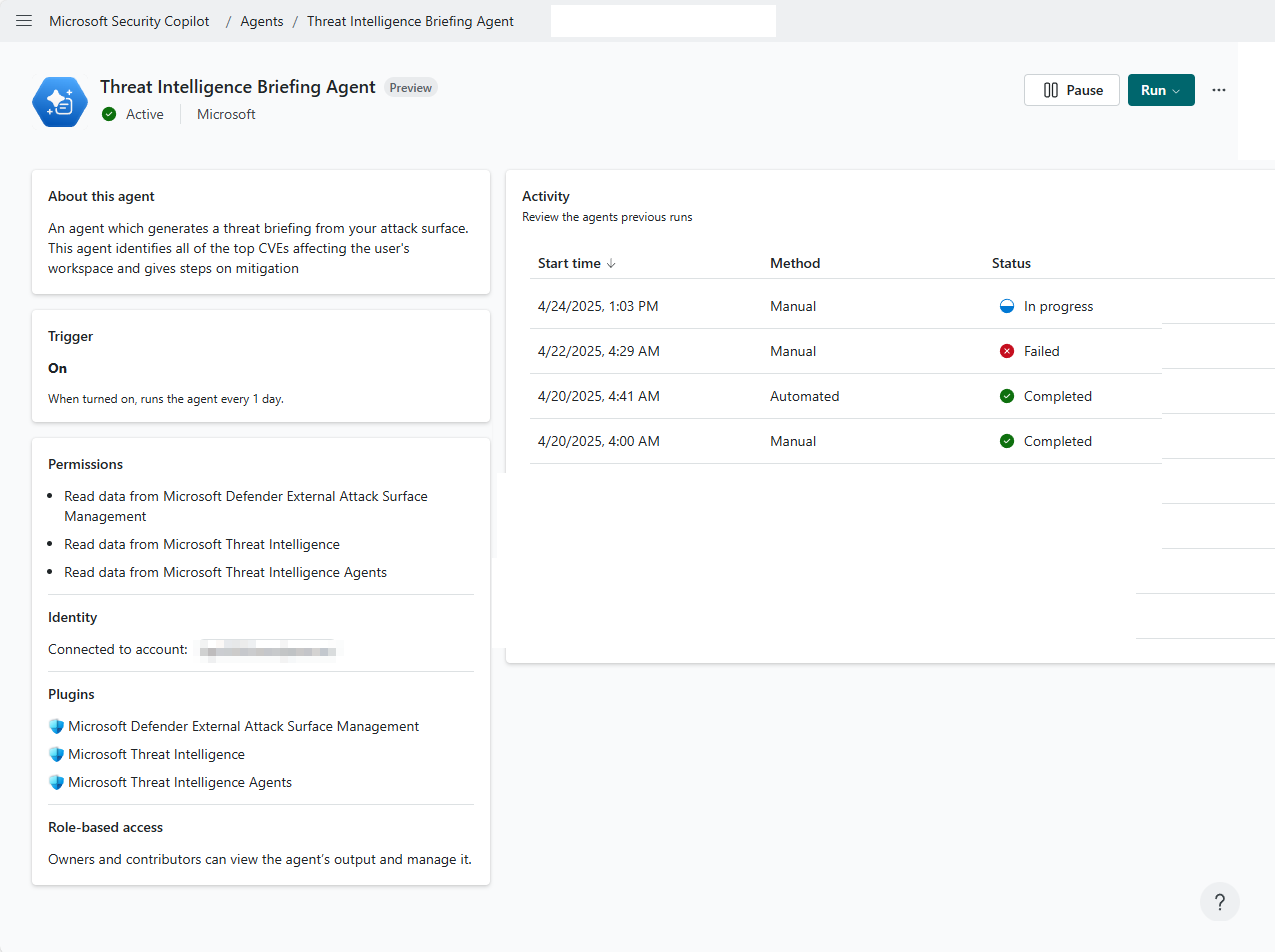
After the agent is created, you’re redirected to the agent overview page. To run the agent, go to the upper right of the page and select Run agent. Select On the trigger to schedule the agent to run at the set time or select One time to run the report on demand.

Assess and provide feedback on the agent’s output
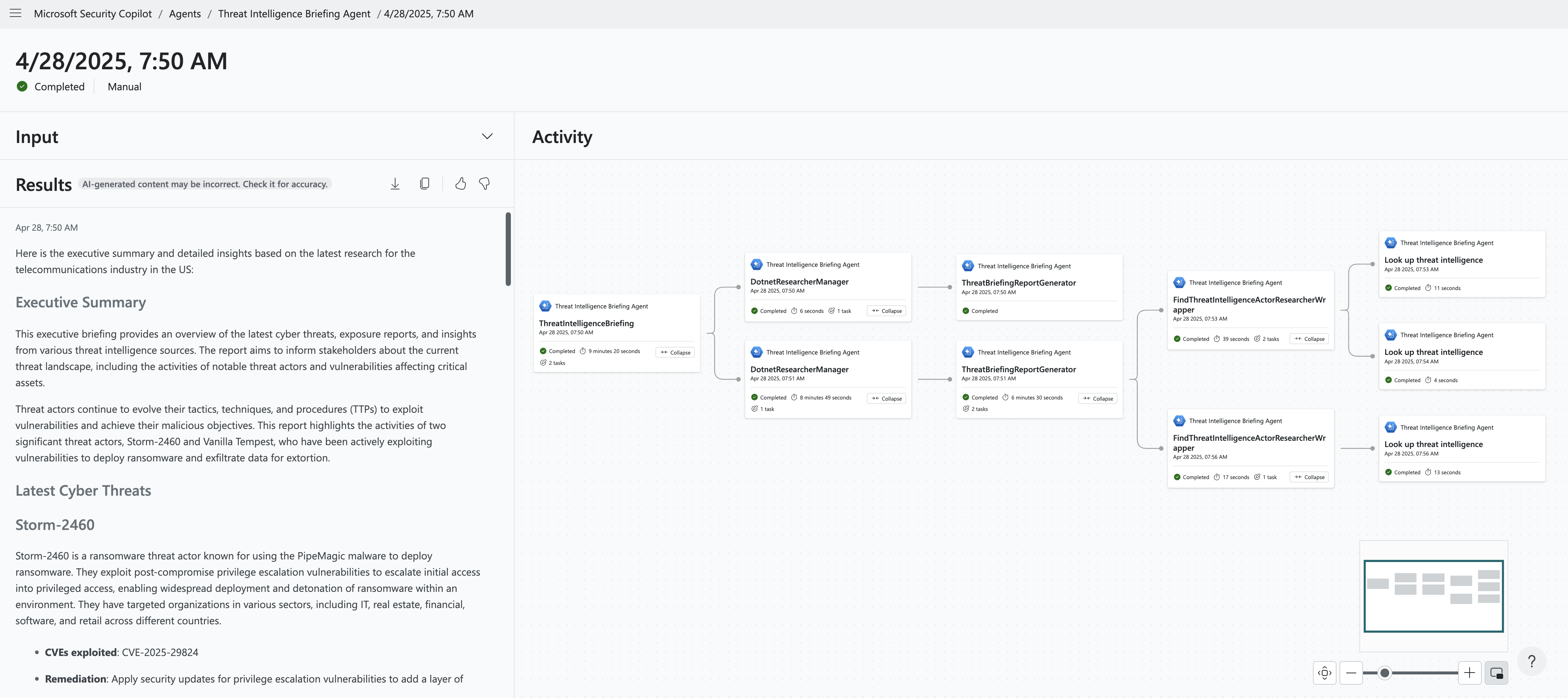
The generated reports appear in the Threat Intelligence Briefing Agent page under Activity. It displays the name of the report, the start time, method of generation, and current status.
Select one of the reports to assess the agent's output.
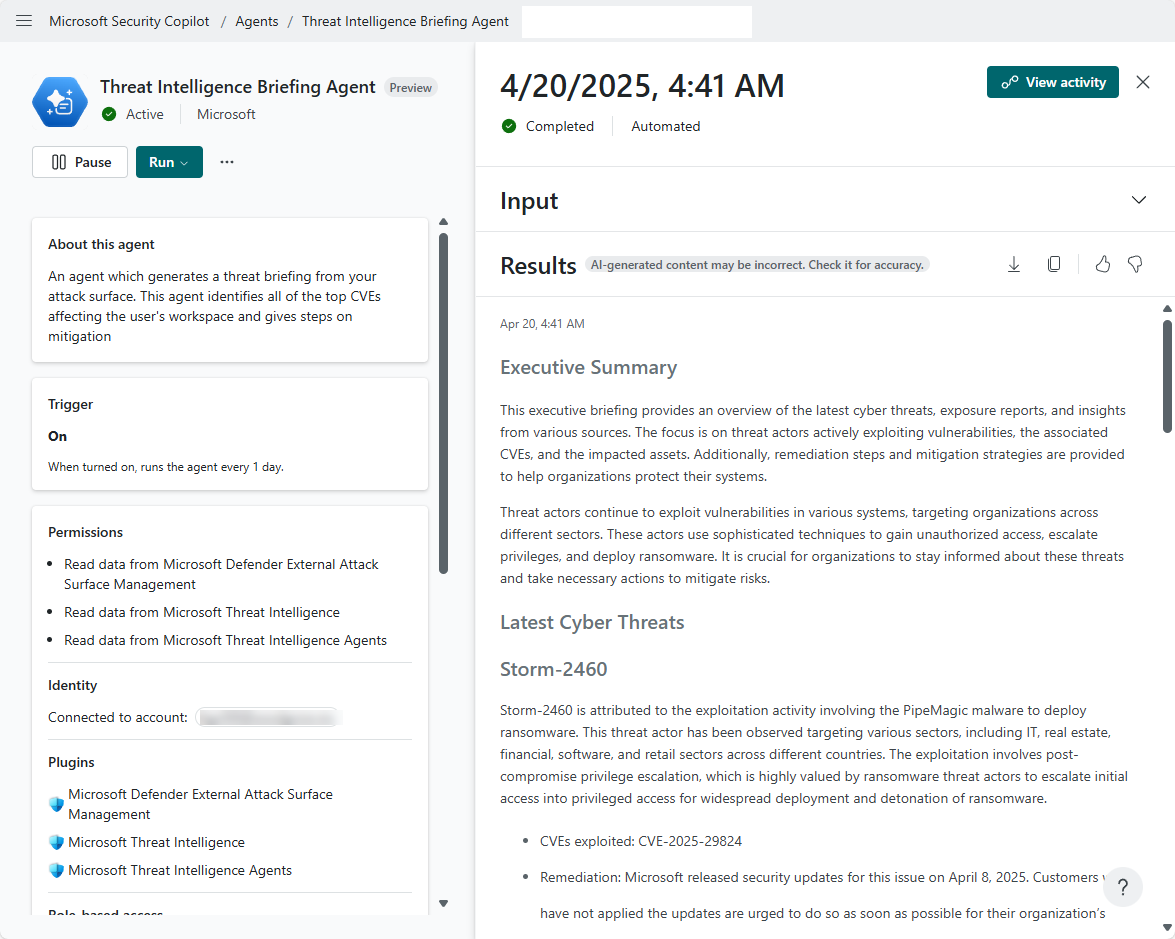
The threat intelligence briefing contains a relevant summary of threat information and detailed technical analysis, including any actively exploited vulnerability and its possible organizational impact.
The Threat Intelligence Briefing Agent dynamically chooses the next step based on the outcome of the previous step as it builds the briefing. You can view the agent’s progress toward producing the threat briefing by selecting View activity.
You'll see details of the activity, providing you with transparency on the steps taken by the agent to produce the output.
You can provide feedback about the briefing by selecting the thumbs up or thumbs down button. You can elaborate in the text box that appears after. Select Submit to give your feedback.