Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
The default email protections in Microsoft 365 protect your organization from spam, malware, phishing and other email threats. These protections are included in all organizations with cloud mailboxes.
These protections are on by default via the default threat policies for:
The default threat policies for these features apply to all recipients. You can't turn them off, but you can override them by turning on and configuring preset security policies or creating custom threat policies.
You can customize the security settings in the default threat policies, create custom threat policies, or better yet, turn on and add all recipients to the Standard and/or Strict preset security policies. For complete information, see Configure threat policies.
The rest of this article explains how the default email protections for cloud mailboxes work and the features they contain.
Tip
The default email protections for cloud mailboxes are also available as a separate subscription to protect on-premises email environments (not just Microsoft Exchange). For more information, see Exchange Online Protection for on-premises organizations.
How the default email protections for cloud mailboxes work
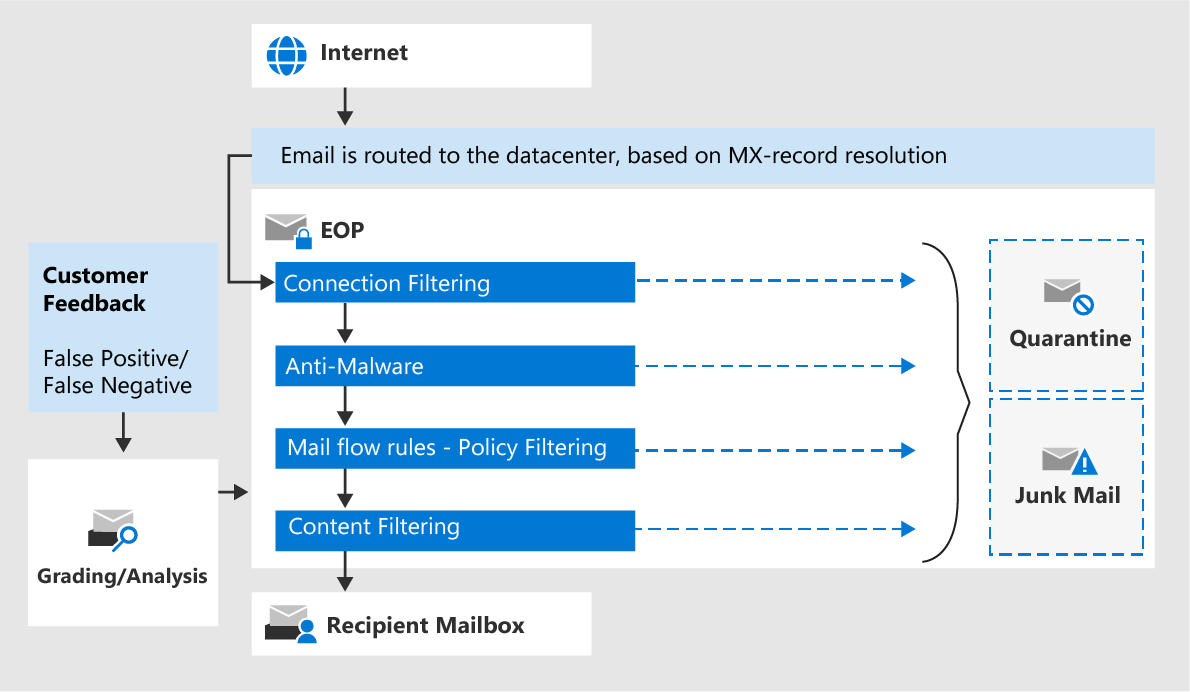
The following diagram shows how the default email protections for cloud mailboxes work.
Incoming messages in Microsoft 365 initially pass through connection filtering, which checks the sender's reputation. Most spam is rejected at this point. For more information, see Configure connection filtering.
If malware is found in the message or a message attachment, the message is delivered to quarantine. By default, only admins can view and interact with malware quarantined messages. But, admins can create and use quarantine policies to specify what users are allowed to do to quarantined messages. To learn more about malware protection, see Anti-malware protection.
Policy filtering evaluates the message against any Exchange mail flow rules (also known as transport rules) configured to act on messages. For example, a rule can notify a manager about messages from a specific sender.
In on-premises organizations with Exchange Enterprise CAL with Services licenses, data loss prevention (DLP) checks also happen at this point.
The message passes through content filtering, which includes anti-spam and anti-phishing filtering:
Anti-spam policies identify messages as bulk, spam, high confidence spam, phishing, or high confidence phishing.
High confidence phishing messages are always delivered to quarantine. By default, only admins can view and interact with high confidence phishing messages.
Anti-phishing policies identify messages as spoofing.
You can configure the action to take on the message based on the filtering verdict (for example, quarantine or move to the Junk Email folder), and what users can do to the quarantined messages using quarantine policies. For more information, see Configure anti-spam policies and Configure anti-phishing policies for all cloud mailboxes.
A message that successfully passes all of these protection layers is delivered to the recipients.
For more information, see Order and precedence of email protection.
Microsoft 365 datacenters
Microsoft 365 runs on a worldwide network of datacenters that are designed to provide the best availability. For example, if a datacenter becomes unavailable, email messages are automatically routed to another datacenter without any interruption in service. Servers in each datacenter accept messages on your behalf, providing a layer of separation between the servers that host your organization and the internet. Through this highly available network, Microsoft can ensure that email reaches your organization in a timely manner.
Microsoft load balances between datacenters withing the same region only. If you're provisioned in one region, all of your messages are processed using the mail routing for that region.
Microsoft 365 communications
The following communication channels are available for issues and new features in Microsoft 365:
- When a Service Level Event affects you, a communication alert (typically accompanied by a bell icon) will appear in the Microsoft 365 admin center at https://admin.microsoft.com. We recommend that you read and act on any items as appropriate.
- The Microsoft 365 Message center at https://admin.microsoft.com/Adminportal/Home?#/MessageCenter also contains information about new and updated features. For more information, see Track new and changed features in the Microsoft 365 Message center.
- The Microsoft 365 roadmap is a good resource for finding out information about upcoming new features.
- We also post blog articles about new features to the Microsoft 365 Blogs website.
Features in the default email protections for cloud mailboxes
This section provides a high-level overview of the main features that are available in the default email protections for cloud mailboxes.
For information about requirements, important limits, and feature availability across all subscription plans, see the Exchange Online Protection service description.
Tip
- Microsoft 365 uses several URL blocklists that help detect known malicious links within messages.
- Microsoft 365 uses a vast list of domains that are known to send spam.
- Microsoft 365 inspects the active payload in the message body and all message attachments for malware.