Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Security is a complex and challenging discipline that you need to consider in nearly all aspects of your cloud and technology environments. Consider these key points:
- Everything is a potential target or attack vector: In today's landscape, attackers can exploit vulnerabilities in an organization's people, processes, and technologies to achieve their malicious objectives.
- Business applications have unique security challenges: Business applications encounter unique security challenges that span across all industries.
- Security requires teamwork: Defending against attacks requires a coordinated effort across business, technology, and security teams. Each team must actively contribute to security initiatives and collaborate effectively.
This Power Platform Adoption security guidance is one component of a larger set of Microsoft security guidance designed to help various teams understand and perform their security responsibilities:
- The Power Platform Adoption security guidance provides security guidance for teams that manage Power Platform environments.
- The Power Platform Well-Architected security guidance provides guidance for individual workload owners about how to apply security best practices to workload development and DevOps and DevSecOps processes.
- The Azure Cloud Adoption Framework Secure methodology provides security guidance for teams that manage the technology infrastructure that supports all the workload development and operations hosted on Azure.
- Microsoft Cloud Security benchmark provides best practice guidance for stakeholders to ensure robust cloud security.
- The Power Platform security and governance documentation provides you with information on how set up and maintain security and governance features for Power Platform.
Throughout your Power Platform adoption journey, look for opportunities to enhance your overall security posture through modernization.
Assess security score and act on recommendations
The Security page in the Power Platform admin center helps you discover and navigate the range of capabilities managed security provides. Start by viewing and managing security tasks, assessing your tenant's security posture, and implementing proactive policies across network security, access control, compliance, and threat detection. Gauge your organization's security posture with the security score, illustrated on a qualitative scale (low, medium, high). Then, act on tailored recommendations to improve your tenant's security score by configuring both proactive and reactive security guardrails, prioritized by level of risk.
The Security page provides a centralized ___location to view and manage security recommendations, assess your security score, and implement proactive policies to safeguard your organization.
Administrators can:
- Assess security score: Understand and improve the organization's security policies with the security score. This score is illustrated on a qualitative scale (low, medium, or high) and helps you measure your organizational security position for Power Platform workloads.
- Act on recommendations: Identify and implement impactful recommendations generated by the system based on best practices to improve your tenant's security score.
- Manage proactive policies: Manage proactive policies for governance and security.
Adopt Zero Trust as a strategy
Adopting Zero Trust as a strategy helps you start your Power Platform adoption journey with a modern approach to security in place. The Zero Trust approach is founded on three principles:
- Verify explicitly. Always authenticate and authorize based on all available data points.
- Use least privilege. Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.
- Assume breach. Minimize the blast radius and segment access. Verify end-to-end encryption, and use analytics to get visibility into activities related to your systems, drive threat detection, and improve defenses.
Microsoft provides a Zero Trust-based security modernization blueprint that organizations can use as a guide.
Enable Managed security features
Managed security is a suite of premium capabilities that offers advanced protection and empowers security administrators to effectively manage and secure access to customer data and resources. It brings together Microsoft's most advanced threat protection, data protection and privacy, identity and access management, and compliance capabilities to help customers meet today's cybersecurity challenges.
We recommend you evaluate and enable managed security features to enhance your security posture.
Security Development Lifecycle
Establish a Security Development Lifecycle (SDL) for Power Platform development to make sure that security is integrated into every phase of the development process. SDL involves a series of practices and procedures designed to identify and mitigate security risks from the initial design stages through to deployment and maintenance. By incorporating security considerations early and throughout the development lifecycle, you can proactively address potential vulnerabilities, reduce the risk of security breaches, and ensure compliance with regulatory requirements.
Learn more: Recommendations for securing a development lifecycle
Training
Provide security training for makers and developers to help them build solutions with Power Platform that are secure and resilient against threats. This training should cover best practices for secure coding, data protection, and compliance with regulatory standards. By educating makers and developers on potential security risks and how to mitigate them, you foster a culture of security awareness and responsibility. Training should include practical exercises, real-world scenarios, and regular updates to keep pace with evolving threats.
- Enhance existing Power Platform trainings by adding information on how to build secure solutions.
- Educate users on your environment and data loss prevention policy strategy and any other configurations that might impact their solutions, and provide guidance on how to request changes.
- Include information on the Security Development Lifecycle (SDL) phases and what users should be aware of to keep their solutions secure.
- Communicate to users how you'll work together to progress through each phase.
Having a central source, such as a SharePoint site or wiki, where makers can easily access this training content is important. Through a centralized repository, all team members have consistent and up-to-date information, making it easier to discover and reference security guidelines and resources. Empowering makers and developers with the knowledge and tools they need helps safeguard your organization's data and applications.
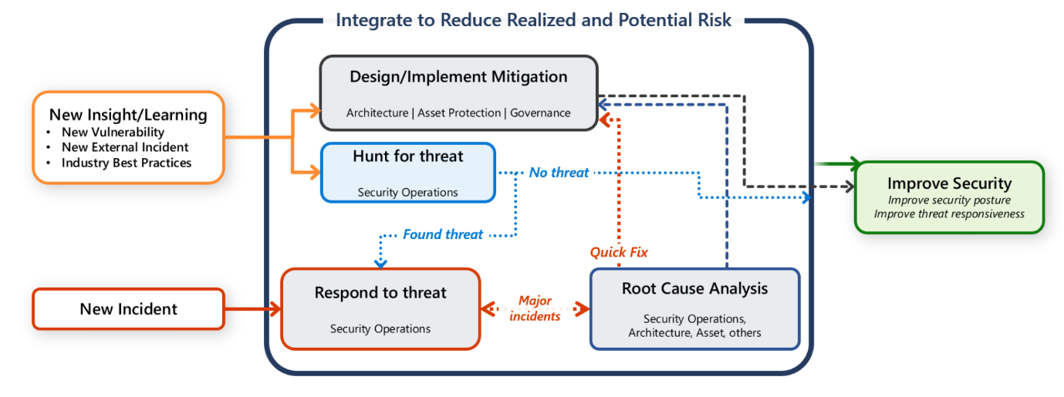
Incident preparation and response
Establish a comprehensive incident response plan that outlines procedures for identifying, managing, and mitigating security incidents. This plan should include clear roles and responsibilities, communication protocols, and steps for containment, eradication, and recovery. Regular training and simulations help ensure that all team members are familiar with the plan and can respond effectively to an incident. Additionally, maintain detailed logs and audit trails to investigate incidents and understand their impact. By being well-prepared and having a robust incident response strategy in place, you can minimize the damage caused by security breaches and quickly restore normal operations.
Integrate Power Platform into your security operations (SecOps) practices to enhance the security and compliance of your low-code/no-code solutions.
Learn more: Recommendations for security incident response
Continuous improvement
The journey toward a modern, robust security posture doesn't end with the initial implementation. To keep up with new threats, continuously review and refine your security practices while maintaining strict adherence to standards. Continuous improvement is essential for maintaining a robust security posture because cyber threats continuously evolve and become more sophisticated. To protect against these ever-changing risks, ensure ongoing enhancements.
Next steps
Review the detailed articles in this series to further enhance your security posture:
- Detect threats to your organization
- Establish data protection and privacy controls
- Implement a DLP strategy
- Configure identity and access management
- Meet compliance requirements
- Secure the default environment
After reviewing the articles, review the security checklist to ensure Power Platform deployments are robust, resilient, and aligned with best practices.