Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The Data Security Investigations (preview) workflow helps you quickly identify, investigate, and take action on data associated with security and data breach incidents. This workflow isn't a linear process. It includes significant iteration requirements for several of the steps to fine tune searches, evidence gathering, classification, and investigation by using AI and activities.
Identifying and taking action on data and access uses the following workflow:
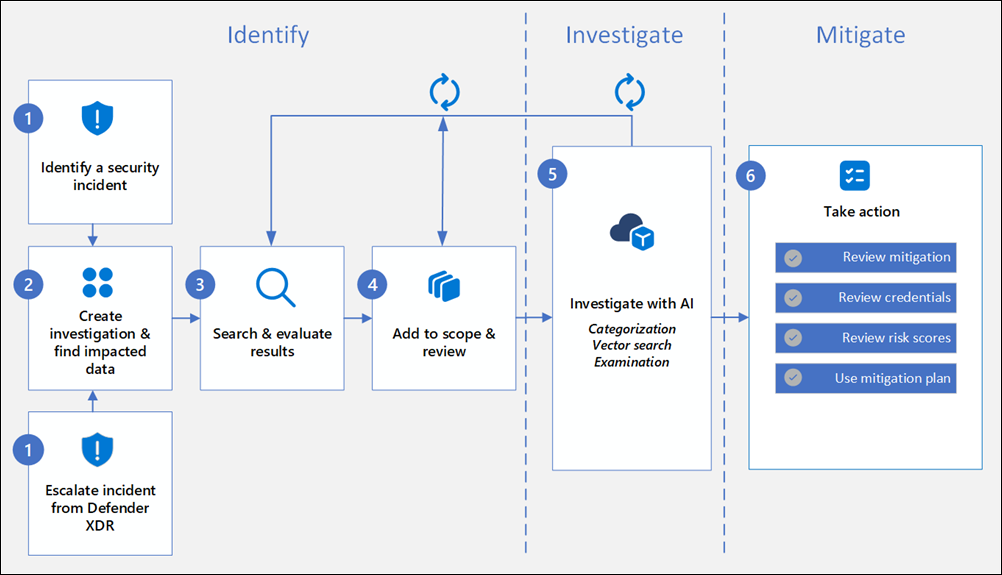
Step 1: Identify and escalate incidents
Identify a data security incident
Data breaches and other data security incidents require quick action to identify and contain potential risks to your organization. It's critical that you quickly identify these incidents and streamline an integrated response. Investigating a data security incident can be daunting. It might include inefficient workflows across multiple tools, manual work, and extra complexity as the investigation grows in size. You might face labor-intensive reviews of impacted data and increased costs.
Data Security Investigations (preview) helps you investigate and mitigate data security incidents and accelerates the time to resolution. After identifying a data security incident, you create a new investigation to enable your data security team to identify incident-related data, conduct deep content analysis, and mitigate risk within one unified solution.
Escalate a data security incident from Microsoft Defender XDR
If you're already using Microsoft Defender XDR in your organization, the integration with Data Security Investigations (preview) allows you to quickly and seamlessly create a new investigation. The investigation automatically includes all incident-related data items from the Defender XDR incident node.
Escalate a data security incident from Insider Risk Management
If you're already using Insider Risk Management in your organization, the integration with Data Security Investigations (preview) allows you to quickly create a new investigation for identified risky user activities.
Step 2: Create an investigation and find impacted data
Creating an investigation in Data Security Investigations (preview) is quick and easy. Depending on your scenario, you can create investigations from:
- Microsoft Defender XDR incidents: Create an investigation from a Defender XDR incident.
- Manually with a search template: Quickly create an investigation by using predefined search templates.
- Manually with full draft mode: Create an investigation by using the full draft mode option to configure specific data sources and search conditions.
Step 3: Search, evaluate results, and review
After creating an investigation, you can review and update data sources. Use search tools to identify items related to the data security incident. This review includes items from the following Microsoft 365 services:
- Exchange Online mailboxes
- SharePoint sites
- OneDrive accounts
- Microsoft Copilot prompts and responses
- Microsoft Teams
You can create and run different searches that are associated with an investigation. Use conditions (such as keywords, file types, incidents, and more) in the query builder to create custom search queries that return results with the data most likely relevant to the data security incident.
Step 4: Add data to the investigation scope
After you review and refine your search query, add all relevant data items to the investigation scope. In this step, you filter and review specific data items. You also identify any items you don't want to review with AI tools in Data Security Investigations (preview).
Step 5 (a): Investigate items
After adding data items to the investigation scope, start refining and narrowing the data to the most relevant items for your investigation. Narrowing the items to the smallest amount of applicable data helps increase the speed and reduce costs associated with AI processing.
In this step, perform the following actions:
- Select specific items to add directly to your mitigation plan if applicable.
- Identify or exclude specific items from AI processing.
- Prepare the data for AI processing. Vectorize all items not excluded to enable semantic searches and categorization of data.
Step 5 (b): Investigate with AI
After preparing data items for AI processing and completing the processing, start using AI-related tools to help narrow the focus of your investigation to only the most impactful and critical items.
Use the following tools and actions in your review to identify and take action on specific data items:
- Use vector search for natural language queries to identify items for review.
- Define and configure AI-driven categories for the content.
- Use built-in examination areas for selected items.
- Select items to add to the mitigation plan.
Important
Storage and AI capacity cost considerations are associated with the usage of each of the AI tools in Data Security Investigations (preview). For more information, see Billing models in Data Security Investigations (preview) and Use AI analysis in Data Security Investigations (preview).
Step 6: Take actions to mitigate
After you identify the most relevant and impactful items associated with the data security incident, take specific actions to help mitigate risks.
- Review mitigation recommendations: When you select items for examination and choose Mitigation as the focus area, the solution creates mitigation recommendations. Automated AI processing identifies related threats and recommends mitigation steps.
- Review credentials examinations: When you select items for examination and choose Credentials as the focus area, the solution identifies credentials and other access asset examinations. AI analysis processing automatically identifies and generates credential details, type, and specific recommendations.
- Review risk examinations: When you select items for examination and choose Risks as the focus area, the solution automatically creates a security risk score and examination. The risk score helps you prioritize mitigation actions for the most impactful and risky data items.
- Use the mitigation plan: After reviewing examinations and recommendations, add specific data items from the investigation scope to the mitigation plan. This plan helps you manage and track the mitigation status for each data item.