Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article uses the process you learned in Design a data loss prevention policy to show you how to create a Microsoft Purview Data Loss Prevention (DLP) policy that helps prevent users from sharing sensitive items via SharePoint and OneDrive withi external users. Work through these scenarios in your test environment to familiarize yourself with the policy creation UI.
For SharePoint and OneDrive, you create a policy to help prevent sharing of sensitive items with external users via SharePoint and OneDrive.
Important
This article presents a hypothetical scenario with hypothetical values. It's only for illustrative purposes. Substitute your own sensitive information types, sensitivity labels, distribution groups, and users.
How you deploy a policy is as important policy design. This article shows you how to use the deployment options so that the policy achieves your intent while avoiding costly business disruptions.
Prerequisites and assumptions
This scenario uses the Confidential sensitivity label, so it requires you to create and publish sensitivity labels. To learn more, see:
- Learn about sensitivity labels
- Get started with sensitivity labels
- Create and configure sensitivity labels and their policies
This procedure uses a hypothetical distribution group Human Resources and a distribution group for the security team at Contoso.com.
This procedure uses alerts, see: Get started with the data loss prevention alerts
Policy intent statement and mapping
We need to block all sharing of SharePoint and OneDrive items to all external recipients that contain social security numbers, credit card data or have the "Confidential" sensitivity label. We do not want this to apply to anyone on the Human Resources team. We also have to meet alerting requirements. We want to notify our security team with an email every time a file is shared and then blocked. In addition, we want the user to be alerted via email and within the interface if possible. Lastly, we don’t want any exceptions to the policy and need to be able to see this activity within the system.
| Statement | Configuration question answered and configuration mapping |
|---|---|
| “We need to block all sharing of SharePoint and OneDrive items to all external recipients...” | - Administrative scope: Full directory - Where to monitor: Data stored in connected sources, SharePoint sites, OneDrive accounts - Conditions for a match: First Condition > Shared outside my org - Action: Restrict access or encrypt the content in Microsoft 365 locations > Block users from receiving email or accessing shared SharePoint, OneDrive > Block only people outside your organization |
| "...that contain social security numbers, credit card data or have the "Confidential" sensitivity label...” | - What to monitor: use the Custom template - Condition for a match: Create a second condition that is joined to the first condition with a boolean AND - Conditions for a match: Second condition, first condition group > Content contains Sensitive info types > U.S. Social Security Number (SSN), Credit Card Number - Condition group configuration Create a second Condition group connected to the first by boolean OR - Condition for a match: Second condition group, second condition > Content contains any of these sensitivity labels > Confidential. |
| “...We don't want this to apply to anyone on the Human Resources team...” | - Where to apply: exclude the Human Resources Team OneDrive accounts |
| "...We want to notify our Security team with an email every time a file is shared and then blocked..." | - Incident reports: Send an alert to admins when a rule match occurs - Send email alerts to these people (optional): add the Security team - Send an alert every time an activity matches the rule: selected - Use email incident reports to notify you when a policy match occurs: On - Send notifications to these people: add individual admins as desired - You can also include the following information in the report: select all options |
| "...In addition, we want the user to be alerted via email and within the interface if possible...” | - User notifications: On - Notify users in Office 365 with a policy tip: selected |
| “...Lastly, we don’t want any exceptions to the policy and need to be able to see this activity within the system...” | -User overrides: not selected |
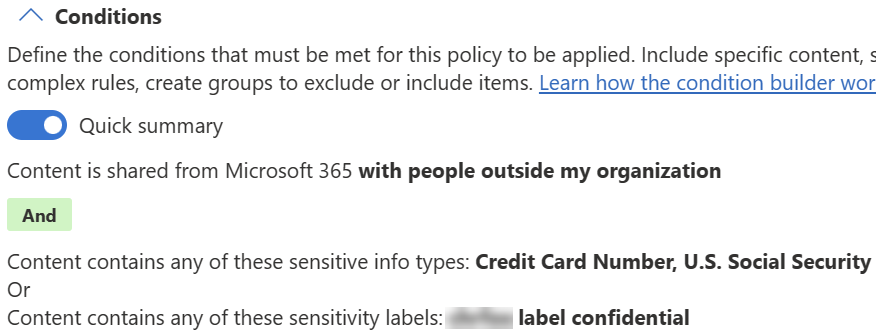
When you configure the conditions, the summary looks like this:
Steps to create policy
Important
For this policy creation procedure, leave the policy turned off. Change these settings when you deploy the policy.
- Sign in to the Microsoft Purview portal.
- Select Data loss prevention > Policies > + Create policy.
- Select Data stored in connected sources.
- Select Custom from both the Categories list and the Regulations list.
- Select Next.
- Enter a Name and a Description for the policy. You can use the policy intent statement here.
Important
You can't rename policies.
- Select Next.
- Accept the default Full directory on the Assign admin units page.
- Select Next.
- Choose where to apply the policy.
- Ensure that the the SharePoint sites and OneDrive accounts locations are selected.
- Deselect all other locations.
- Select Edit in the Actions column next to OneDrive accounts.
- Select All users and groups and then select Exclude users and groups.
- Select +Exclude and then Exclude groups.
- Select Human Resources.
- Select Done and then select Next.
- On the Define policy settings page, the Create or customize advanced DLP rules option should already be selected. Select Next.
- On the Customize advanced DLP rules page, select + Create rule.
- Give the rule a Name and a description.
- Select Add condition and use these values:
- Select Content is shared from Microsoft 365.
- Select with people outside my organization.
- Select Add condition to create a second condition and use these values.
- Select Content contains.
- Select Add > Sensitivity labels > and then Confidential.
- Select Add.
- Under Actions, add an action with these values:
- Restrict access or encrypt the content in Microsoft 365 locations.
- Block only people outside your organization.
- Set the User Notifications toggle to On.
- Select Notify users in Office 365 services with a policy tip and then select Notify the user who sent, shared, or last modified the content.
- Under User overrides, make sure that Allow override from M365 services is NOT selected.
- Under Incident reports:
- Set Use this severity level in admin alerts and reports to Low.
- Set the toggle for Send an alert to admins when a rule match occurs to On.
- Under Send email alerts to these people (optional), choose + Add or remove users and then add the email address of the security team.
- Select Save and then select Next.
- On the Policy mode page, choose Run the policy in simulation mode and Show policy tips while in simulation mode.
- Select Next and then select Submit.
- Select Done.