Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Azure DevOps Services | Azure DevOps Server 2022 - Azure DevOps Server 2019
A Personal Access Token (PAT) serves as an alternative password for authenticating into Azure DevOps. This PAT identifies you and determines your accessibility and scope of access. Treat PATs with the same level of caution as passwords.
When you use Microsoft tools, your Microsoft account (MSA) or Microsoft Entra ID is recognized and supported. If you use tools that don't support Microsoft Entra accounts or don't want to share your primary credentials, PATs can be a suitable alternative. However, we recommend using Microsoft Entra tokens over PATs whenever possible.
Important
We recommend the more secure Microsoft Entra tokens over higher-risk personal access tokens. Learn more about our efforts to reduce PAT usage. Review our authentication guidance to choose the right authentication mechanism for your needs.
Prerequisites
| Category | Requirements |
|---|---|
| Permissions | Permission to access and modify your user settings where PATs are managed. - Go to your profile and select User settings > Personal access tokens. If you can see and manage your PATs here, you have the necessary permissions. - Go to your project and select Project settings > Permissions. Find your user account in the list and check the permissions assigned to you. Look for permissions related to managing tokens or user settings. - If your organization has policies in place, an administrator might need to grant you specific permissions or add you to an allowlist to create and manage PATs. - PATs are connected to the user account that minted the token. Depending on the tasks the PAT performs, you might need more permissions yourself. |
| Access levels | At least Basic access. |
| Tasks | Use PATs only when necessary and always regularly rotate them. See our section on Best Practices when using PATs. |
Create a PAT
Sign in to your organization (
https://dev.azure.com/{Your_Organization}).From your home page, open user settings
 and select Personal access tokens.
and select Personal access tokens.
Select + New Token.

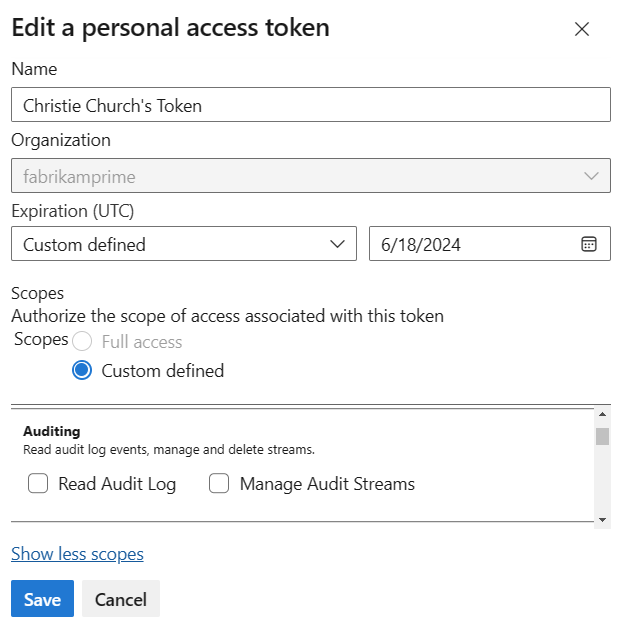
Name your token, select the organization where you want to use the token, and then set your token to automatically expire after a set number of days.

Select the scopes for this token to authorize for your specific tasks.
For example, to create a token for a build and release agent to authenticate to Azure DevOps, set the token's scope to Agent Pools (Read & manage). To read audit log events and manage or delete streams, select Read Audit Log, and then select Create.

Note
Your admin(s) may restrict you from creating full-scoped PATs or limit you to packaging-scope PATs only. Reach out to your admin to get on the allowlist if you need access to additional scopes. Some scopes, e.g.
vso.governance, may not be available in the UI if they aren't for widespread public use.When you're done, copy the token and store it in a secure ___location. For your security, it doesn't display again.

Use your PAT anywhere your user credentials are required for authentication in Azure DevOps.
Important
- Treat a PAT with the same caution as your password and keep it confidential. DO NOT SHARE PATS.
- For organizations backed by Microsoft Entra ID, you must sign in with your new PAT within 90 days or it will become inactive. For more information, see User sign-in frequency for Conditional Access.
Notifications
During the lifespan of a PAT, users receive two notifications: at time of creation and three days before expiration.
After you create a PAT, you may receive a notification similar to below. This notification serves as confirmation that your PAT was successfully added to your organization.

An expiration notification email will be sent three days prior to expiration. If your admin has removed your ability to create PATs in the organization, the email will indicate that it is no longer possible for you to regenerate PATs. Reach out to your Project Collection Administrator to be included in an allowlist for continued PAT creation permissions in that organization.
For more information, see Configure an SMTP server and customize email for alerts and feedback requests.
Unexpected notification
If you receive an unexpected PAT notification, it might mean that an administrator or tool created a PAT for you. Here are some examples:
- A token named "git:
https://dev.azure.com/{Your_Organization}on YourMachine" gets created when you connect to an Azure DevOps Git repo via git.exe. - A token named "Service Hooks: Azure App Service: Deploy web app" gets created when you or an administrator sets up an Azure App Service web app deployment.
- A token named "WebAppLoadTestCDIntToken" gets created when web load testing gets set up as part of a pipeline by you or an administrator.
- A token named "Microsoft Teams Integration" gets created when a Microsoft Teams Integration Messaging Extension gets set up.
Warning
- Revoke the PAT (and change your password) if you suspect it exists in error.
- Check with your administrator if you're a Microsoft Entra user to see if an unknown source or ___location accessed your organization.
- Review the FAQ on accidental PAT check-ins to public GitHub repositories.
Use a PAT
Your PAT serves as your digital identity, much like a password. You can use PATs as a quick way to do one-off requests or prototype an application locally. Use a PAT in your code to authenticate REST APIs requests and automate workflows by including the PAT in the authorization header of your request.
Important
Once your app code is working, switch to Microsoft Entra OAuth to acquire tokens on-behalf-of your app's users or a service principal or managed identity to acquire tokens as an application. It is not recommended to keep running apps or scripts with PATs long-term. Microsoft Entra tokens can be used anywhere a PAT is used. Consider acquiring a Microsoft Entra token via the Azure CLI for ad-hoc requests.
To provide the PAT through an HTTP header, you must first convert it to a Base64 string. It can then be provided as an HTTP header in the following format.
Authorization: Basic BASE64_USERNAME_PAT_STRING