Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
With Copilot Studio, you can rapidly build and roll out high-value agents for your users that can connect with many data sources and services. Some of these sources and services might be external, non-Microsoft services, and might even include social networks, alongside connections to your organizational data.
Organizational data is the most important asset administrators are responsible for safeguarding. The ability to use that data in a protected way, while still connecting and interacting with other services and systems, is a cornerstone of data security.
Data policies let you govern how agents connect and interact with data and services, within and outside your organization. Administrators can configure Copilot Studio and Power Platform data policies in the Power Platform admin center.
Important
In early 2025, data policy enforcement for all tenants is set to Enabled by default, as announced in the message center alert MC973179: Copilot Studio - Upcoming updates to data loss prevention enforcement.
Learn about troubleshooting enforcement in your tenant.
Prerequisites
- You should review concepts about Data policies
- You must be a tenant admin or have the Environment Admin role
Copilot Studio connectors and data groups
Copilot Studio connectors can be classified within a data policy under the following data groups, which are presented in the Power Platform admin center when reviewing data policies:
- Business
- Non-business
- Blocked
You can use the connectors for data policies to protect your organization's data from any malicious or unintentional data exfiltration by your agent makers.
The default group in data policies is a category where connectors are automatically added when no explicit grouping is defined during their introduction. Connectors introduced after 2019, such as Chat without Microsoft Entra ID authentication or Direct Line Channels, are likely to have been added to the default "Non-business" group.
In many organizations, connectors in the "Non-business" group are automatically blocked. If a Copilot Studio data policy connector is blocked in your tenant, you should review which data group the connector has been added to.
Administrators can configure default groups at the data policy level, within the Power Platform admin center.
Important
Copilot Studio supports data policy enforcement in real time. Agent makers and users see error messages for any data policy violation.
In a data policy, the connectors must be in the same data group because data can't be shared among connectors that are in different groups.
You can configure data policies in the Power Platform admin center to block any of the following Copilot Studio connectors.
| Connector name | Use case |
|---|---|
| Application Insights in Copilot Studio | Block agent makers from connecting agents with Application Insights. |
| Chat without Microsoft Entra ID authentication in Copilot Studio | Block agent makers from publishing agents that aren't configured for authentication. Agent users must authenticate themselves to chat with the agent. For more information, see Data policy example - Require user authentication in agents. |
| Direct Line channels in Copilot Studio | Block agent makers from enabling or using Direct Line channel. For example, the Demo website, Custom website, Mobile app, and other Direct Line channels would be blocked. |
| Facebook channel in Copilot Studio | Block agent makers from enabling or using the Facebook channel. |
| Knowledge source with SharePoint and OneDrive in Copilot Studio | Block agent makers from publishing agents configured with SharePoint as a knowledge source. Supports Data policy connector endpoint filtering to allow or deny endpoints. |
| Knowledge source with documents in Copilot Studio | Block agent makers from publishing agents configured with documents as a knowledge source. |
| Knowledge source with public websites and data in Copilot Studio | Block agent makers from publishing agents configured with public websites as a knowledge source. Supports Data policy connector endpoint filtering to allow or deny endpoints. |
| Microsoft Copilot Studio | Block agent makers from using event triggers in Copilot Studio agents. For more information, see Data policy example - Block event triggers in agents. |
| Microsoft Teams channel in Copilot Studio | Block agent makers from enabling or using the Teams channel. |
| Omnichannel in Copilot Studio | Block agent makers from enabling or using the Omnichannel channel. |
| Skills with Copilot Studio | Block agent makers from using skills in Copilot Studio agents. For more information, see Data policy example - Block skills in agents and Data policy example - Block HTTP requests in agents. |
Identify and troubleshoot the impact of data policies
To find agents that your organization's data policies might affect, you can:
Use the Power BI dashboard of the Center of Excellence (CoE) Starter Kit to get a list of agents in your organization. Go to the Copilot Studio overview page on the CoE Dashboard to see the agents and environment names in your organization.
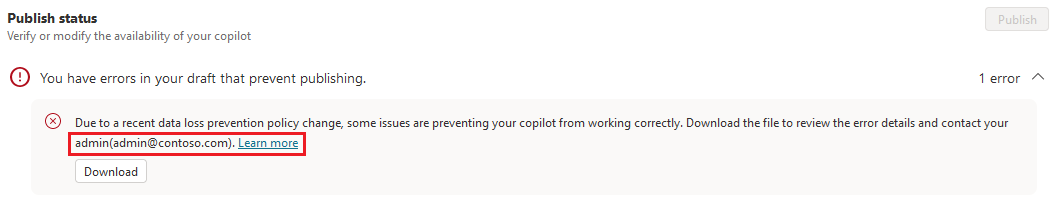
Run a campaign with the agent makers in your organization to address data policy errors or updated data policies. You can download all agent data policy errors by selecting Details in the error notification banner and selecting Download from the error message details.
If data policies are affecting the functionality of your agents, see Troubleshoot data policies for Copilot Studio.
Example data policy configurations
To get started with Copilot Studio agent governance, review the following example scenarios:
- Data policy example - Require user authentication in agents
- Data policy example - Block SharePoint knowledge source in agents
- Data policy example - Block Power Platform Connectors in agents
- Data policy example - Block HTTP requests in agents
- Data policy example - Block skills in agents
- Data policy example - Block event triggers in agents
- Data policy example - Block channels to disable agent publish
Important
Agent data policy enforcement exemption is no longer supported. Agents that were previously exempted from data policy enforcement have their enforcement set to Soft-enabled since January 2025, and set to Enabled since February 2025.
Add and update the learn-more and admin contact email links
You can use the Set-PowerAppDlpErrorSettings PowerShell cmdlet to add an email address and a "Learn more" link to the data policy error messages.
To add the email address and learn-more link for the first time, run the following PowerShell script, replacing the values for the <email>, <URL>, and <tenant ID> parameters with your own.
$ContactDetails = [pscustomobject] @{
Enabled=$true
Email="<email>"
}
$ErrorMessageDetails = [pscustomobject] @{
Enabled=$true
Url="<URL>"
}
$ErrorSettingsObj = [pscustomobject] @{
ErrorMessageDetails=$ErrorMessageDetails
ContactDetails=$ContactDetails
}
New-PowerAppDlpErrorSettings -TenantId "<tenant ID>" -ErrorSettings $ErrorSettingsObj
To update an existing configuration, use the same PowerShell script, and replace New-PowerAppDlpErrorSettings with Set-PowerAppDlpErrorSettings.
Warning
These settings apply to all Power Platform apps within the specified tenant.